Spotiamp (spotify) with Milkdrop preconfigured.
Spotiamp is for spotify premium subscribers only.
So maybe you tried milkdrop for winamp in the past and loved it but want to enjoy the milkdrop visualization with your spotify music. Recently spotiamp has been released (more info at spotiamp.com) which is a winamp style spotify player. Configuring milkdrop to work on spotify is slightly more complicated than it should be. To simplify things we have preconfigured it for you in a zipped up folder. Follow these instructions to get it working.
Be advised spotiamp is still a little buggy, click on eject button to select playlists.
1. Download the zip file from http://www.computerrepairtech.com/spotiamp_0.2_md.zip
2. Extract the zip file to the location of your choice.
3. Run Spotiamp.exe from the location you extracted the files to.
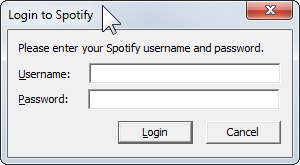
4. You should be prompted for your spotify login info. Login.
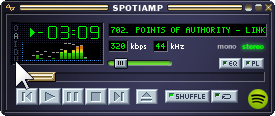
5. Once logged in go ahead and start playing some music then click here on the hard to see “V”
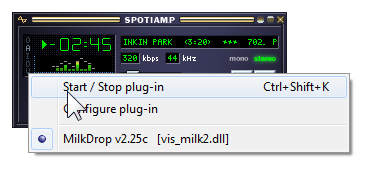
6. Click “Start / Stop plug-in”
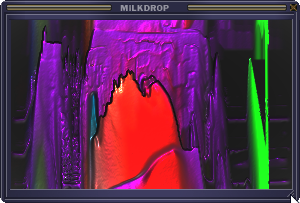
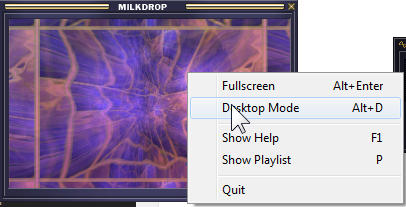
7. You should see a window that looks like this, you can resize it by dragging the bottom left corner:
8. To activate desktop mode the coolest feature of milkdrop right click the window then click desktop mode.
9. Take a look at your desktop wallpaper now. To stop the wallpaper milkdrop just click on it then hit ESC. Pushing F1 will bring up help options. Once you close the milkdrop you may have to relaunch spotiamp to get it working again its a little buggy.